Open 13+ pages which of the following best describes a rootkit analysis in Google Sheet format. Software hidden on a computer for the purpose of compromising the system. The term zombie is _____. Software used for the collection of personal data. Check also: describes and which of the following best describes a rootkit Currently there are many tools that have the ability to detect any type of virus but it is strongly recommended to use the best tools to scan the software for a rootkit.
D A lack of fear of being caught. 14Which of the following is the primary objective of a rootkit.

Windows 10 S Free Upgrade Offer Is Over What Now Windows 10 Windows 10 Microsoft Windows System Which of the following BEST describes the type of malware infecting this companys network.
| Topic: A program that easily can hide and allow someone to take full control of your computer from a remote location. Windows 10 S Free Upgrade Offer Is Over What Now Windows 10 Windows 10 Microsoft Windows System Which Of The Following Best Describes A Rootkit |
| Content: Synopsis |
| File Format: DOC |
| File size: 1.7mb |
| Number of Pages: 26+ pages |
| Publication Date: August 2021 |
| Open Windows 10 S Free Upgrade Offer Is Over What Now Windows 10 Windows 10 Microsoft Windows System |
 |
Software that provides the originator with the venue to propagate.

It replaces legitimate programs. Rootkit or rootkit virus is a form of malware. A A disregard for the law. The first word is root as the superuser under Linux and Unix operating system. 18Which of the following terms is used to describe a program that hides in a computer and allows someone from a remote location to take full control of the computer. Which of the following BEST describes the type of malware the analyst discovered.

Home Scan Rootkit Resides below regular antivirus software detection.
| Topic: Requires administrator privileges for installation and then maintains those privileges to allow subsequent access. Home Scan Rootkit Which Of The Following Best Describes A Rootkit |
| Content: Explanation |
| File Format: Google Sheet |
| File size: 2.1mb |
| Number of Pages: 24+ pages |
| Publication Date: December 2019 |
| Open Home Scan Rootkit |
 |

The Rootkit Qna Scan Rootkit You have heard about a new malware program that presents itself to users as a virus scanner.
| Topic: 13Subsequent analysis determined that proprietary data would have been deleted from both the local server and backup media immediately following a specific administrators removal from an employee list that is refreshed each evening. The Rootkit Qna Scan Rootkit Which Of The Following Best Describes A Rootkit |
| Content: Answer |
| File Format: Google Sheet |
| File size: 2.3mb |
| Number of Pages: 25+ pages |
| Publication Date: July 2018 |
| Open The Rootkit Qna Scan Rootkit |
 |

On Desktop Instead its a slew of distinct malicious applications that take advantage of a security flaw to infiltrate a computer and give hackers persistent remote access to it.
| Topic: 23Which Of The Following Best Describes a Rootkit A rootkit is a term that refers to a collection of malware. On Desktop Which Of The Following Best Describes A Rootkit |
| Content: Learning Guide |
| File Format: Google Sheet |
| File size: 3.4mb |
| Number of Pages: 8+ pages |
| Publication Date: May 2021 |
| Open On Desktop |
 |

Clean Slow Windows Pc Laptop From Spyware Malware Viruses Worms And Trojans Anti Malware Program Arsenal Malwaretes Malware Malware Removal To return fake manipulate data in the chain.
| Topic: 1The next morning however the HIDS once again started alerting on the same desktops and the security team discovered the files were back. Clean Slow Windows Pc Laptop From Spyware Malware Viruses Worms And Trojans Anti Malware Program Arsenal Malwaretes Malware Malware Removal Which Of The Following Best Describes A Rootkit |
| Content: Synopsis |
| File Format: Google Sheet |
| File size: 3.4mb |
| Number of Pages: 45+ pages |
| Publication Date: March 2021 |
| Open Clean Slow Windows Pc Laptop From Spyware Malware Viruses Worms And Trojans Anti Malware Program Arsenal Malwaretes Malware Malware Removal |
 |

Using Rsca To Help You Understand What Your Iis Server Requests Are Doing Server Understanding Helpful Rootkits using a special technique to manipulate the behavior of the environment it is running on.
| Topic: Time bomb D. Using Rsca To Help You Understand What Your Iis Server Requests Are Doing Server Understanding Helpful Which Of The Following Best Describes A Rootkit |
| Content: Summary |
| File Format: Google Sheet |
| File size: 2.6mb |
| Number of Pages: 35+ pages |
| Publication Date: August 2017 |
| Open Using Rsca To Help You Understand What Your Iis Server Requests Are Doing Server Understanding Helpful |
 |
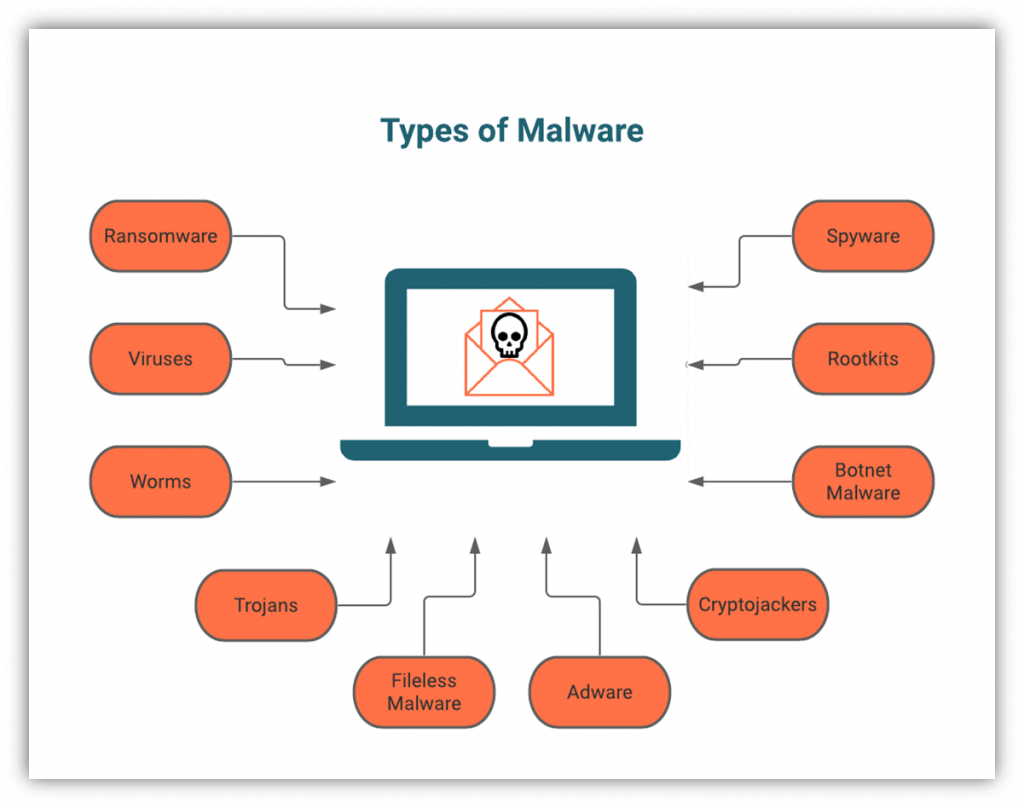
An Informative Guide That Describes The Iso Iec 19770 Standard And Its Applicability To The E Life Cycle Management Life Cycles Software Development Life Cycle A rootkit is a set of programs that allow attackers to maintain hidden permanent administrator-level access to a computer.
| Topic: 9Answer Which of the following best describes a rootkit. An Informative Guide That Describes The Iso Iec 19770 Standard And Its Applicability To The E Life Cycle Management Life Cycles Software Development Life Cycle Which Of The Following Best Describes A Rootkit |
| Content: Answer |
| File Format: DOC |
| File size: 810kb |
| Number of Pages: 8+ pages |
| Publication Date: August 2019 |
| Open An Informative Guide That Describes The Iso Iec 19770 Standard And Its Applicability To The E Life Cycle Management Life Cycles Software Development Life Cycle |
 |
Malware Vs Virus A 4 Minute Explanation Of The Differences A rootkit is a stealthy type of software typically malicious designed to hide the existence of certain processes or programs from normal methods of detection and enable continued privileged access to a computer.
| Topic: 24Which of the following best describes a rootkit. Malware Vs Virus A 4 Minute Explanation Of The Differences Which Of The Following Best Describes A Rootkit |
| Content: Explanation |
| File Format: Google Sheet |
| File size: 800kb |
| Number of Pages: 24+ pages |
| Publication Date: December 2021 |
| Open Malware Vs Virus A 4 Minute Explanation Of The Differences |
 |

Rootkits How Can You Protect Yourself Against Them Ionos You have heard about a new malware program that presents itself to users as a virus scanner.
| Topic: Hiding information within a picture or concealing it in an audio format Allowing the public to use your private key. Rootkits How Can You Protect Yourself Against Them Ionos Which Of The Following Best Describes A Rootkit |
| Content: Synopsis |
| File Format: DOC |
| File size: 3.4mb |
| Number of Pages: 8+ pages |
| Publication Date: January 2020 |
| Open Rootkits How Can You Protect Yourself Against Them Ionos |
 |

Cybersecurity Primer Information Security Awareness Importance Of Cybersecurity The first word is root as the superuser under Linux and Unix operating system.
| Topic: A A disregard for the law. Cybersecurity Primer Information Security Awareness Importance Of Cybersecurity Which Of The Following Best Describes A Rootkit |
| Content: Answer Sheet |
| File Format: DOC |
| File size: 2.8mb |
| Number of Pages: 29+ pages |
| Publication Date: April 2021 |
| Open Cybersecurity Primer Information Security Awareness Importance Of Cybersecurity |
 |

On English
| Topic: On English Which Of The Following Best Describes A Rootkit |
| Content: Explanation |
| File Format: PDF |
| File size: 1.8mb |
| Number of Pages: 9+ pages |
| Publication Date: December 2018 |
| Open On English |
 |

How To Prevent Malware Attacks 7 Ways
| Topic: How To Prevent Malware Attacks 7 Ways Which Of The Following Best Describes A Rootkit |
| Content: Answer |
| File Format: PDF |
| File size: 1.9mb |
| Number of Pages: 13+ pages |
| Publication Date: March 2017 |
| Open How To Prevent Malware Attacks 7 Ways |
 |
Its definitely simple to get ready for which of the following best describes a rootkit Clean slow windows pc laptop from spyware malware viruses worms and trojans anti malware program arsenal malwaretes malware malware removal an informative guide that describes the iso iec 19770 standard and its applicability to the e life cycle management life cycles software development life cycle rootkits how can you protect yourself against them ionos how to prevent malware attacks 7 ways windows 10 s free upgrade offer is over what now windows 10 windows 10 microsoft windows system super saturday craft kits lds crafts craft quotes super saturday crafts birthday gifts for grandma using rsca to help you understand what your iis server requests are doing server understanding helpful on desktop
0 Comments